Secure Remote Access to your Mac using SSH - Part 2

This section will describe the process to create the encryption keys to replace the standard, insecure password authentication and how to setup port forwarding on your router.
Quick Nav:
Step 1: Encryption Key Creation
1. Open a Terminal session and make sure you are in your Home directory.
2. Type the following command to get a full directory listing.
ls -a
3. Make sure the hidden directory .ssh exists. If it doesn’t you will need to create it with the mkdir .ssh command.
4. Change into the .ssh folder using the following command:
cd .ssh
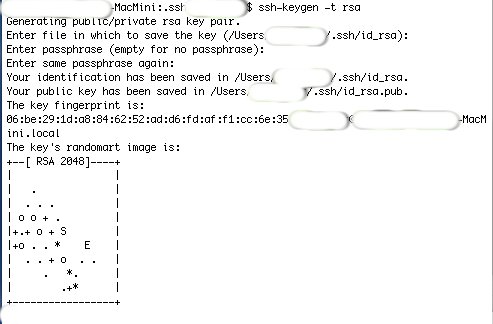
5. Create the encryption keys. Type the command: ssh-keygen -t rsa
6. The system will prompt you for the filename and directory as to where to create the key. Accept the Default.
7. The system will then prompt you for your Passphrase. Use a Passphrase that you will be able to remember and make it as
long as practical, remembering to use letters, numbers and symbols.
8. Repeat the same Passphrase when prompted a second time.
9. When finished, the system will display the Key Fingerprint and the Key’s Randomart Image.
10. The key files are located in the .ssh folder and are named id_rsa and id_rsa.pub
11. Next copy the Public Key into the authorized_keys file, by typing:
cat id_rsa.pub > authorized_keys
12. Now your Private Key needs to be copied to the machine you will be connecting from.
Step 2: Copy Private Key to Machine you will be connecting from.
1. Goto Finder by clicking anywhere on the Desktop
2. On the menu, select Go to Folder and type ~/.ssh. This will open a windows of the hidden .ssh folder.
3. Copy the Private Key - id_rsa to a thumbdrive to be able to copy to the other machine.
4. The Private Key needs to be placed in the .ssh folder on the other machine. If the folder does not exist, create it using the
mkdir .ssh under your Home folder.
Step 3: Connecting from Your laptop using the Keys
1. Now we are ready to connect using the keys. (We are still located on the same internal network).
2. On your laptop, open a Terminal session and enter the following command:
ssh username@local-ip-address
Tiger users will need to use to -i flag to define where the private key is located, as follows:
ssh -i ~/.ssh/id_rsa username@local-ip-address
3. The system will then prompt you to enter the passphrase associated with your key. Enter the passphrase.
4. If successful, the warning banner will be displayed and you will be logged in. Remember that you did not authenticate with
the passphrase, but instead entering the passpharse “unlocked” the private key and used that to authenticate.
Step 4: Setting up your Router for Remote Access
Since there are so many different routers available, these instructions will be generic. Check you router manual for exact instructions for these changes.
1. On your router or computer make sure that the computer you just setup always gets the same TCP/IP address by either statically assigning an address or setting up a
DHCP reservation in the router.
2. SSH uses TCP port 22
- Do NOT change the internal port since we didn’t change that setting on the Mac.
- Change the external TCP port on the router to something different, so someone with a port scanner cannot easily find the SSH port
We recommend a high port number, anything above 2000. In order to identify the setting in the future, you can leave 22 in port number.
In this example, we’ll use 8822.
3. In the router configuration, set up Port Translation to redirect any outside calls to TCP port 8822 to foward that traffic to TCP port 22 at the local-ip-address of your Mac.
4. To connect from outside your local network, use the following command:
ssh -p 8822 username@external-ip-address
where external-ip-address is the external address of your router.
If you router does not support port translation then you’ll need to change the TCP port number in the Mac’s configuration file and do straight-through port forwarding.
You should now be able to connect to your Mac from anywhere on the Internet, using key authentication and encrypted traffic between the computers.
This completes Part 2 of this tutorial.
In Part 3, we will describe some of the programs you can use over your encrypted connection to transfer files and remotely control your home computer.
Remote Access, SSH, VPN






One Comment